Cleo Software Vulnerability: Mitigating Risks, & Staying Protected
If your company uses Cleo software, it’s crucial to be aware of a recent vulnerability that could expose your business to cyber threats. A flaw in...
4 min read
Gleimi De Jesus : Mar 18, 2024 12:25:00 PM
In today’s fast-paced digital world, simplicity is often the key to robust cybersecurity defenses. At the heart of this simplicity lies awareness—an essential yet often overlooked tool. But cybersecurity awareness isn’t one-size-fits-all. People learn in different ways, from visual learners to hands-on problem-solvers. Recognizing these differences is crucial to building an effective training program that resonates with your team and empowers them to protect your business.
Learn more about our training program today and turn awareness into a powerful tool for your business's security! For a condensed version of this article click on our one pager below.
As cyber threats grow, so do the expectations of cyber insurance providers. Many now require organizations to implement cybersecurity awareness training as a condition of coverage. Failing to meet these requirements can leave your business vulnerable—not just to cyberattacks but also to denied insurance claims.
Pro Tip: Our training programs are designed to help you meet these requirements while strengthening your security posture.
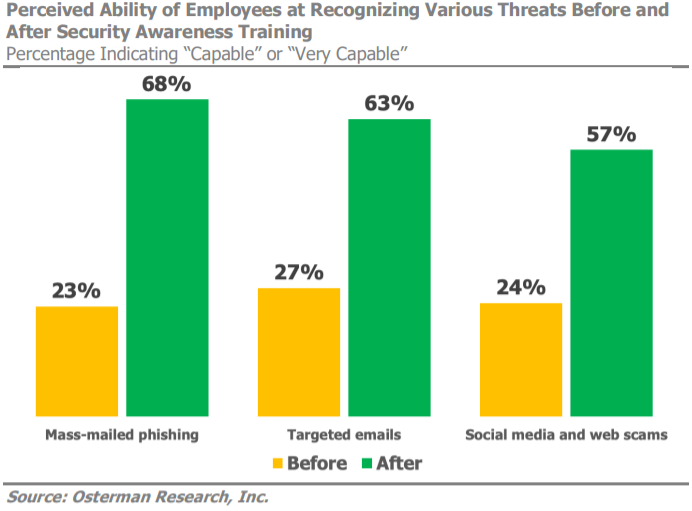
Did you know that human error causes the majority of security breaches? Even the most sophisticated software won’t protect you if your employees accidentally click on phishing links or fall victim to scams. That’s why it’s vital to provide training that equips your team with the skills to recognize and prevent threats.
Curious about your company’s exposure on the dark web? Request your free exclusive report and uncover vulnerabilities before they become liabilities.
Cybersecurity isn’t static, and neither should your training be. Breach Secure Now’s approach is grounded in continuous learning, offering adaptive programs that evolve alongside emerging threats and changing work habits.
What does this mean for you?
Example: A one-time training on phishing might teach your team the basics, but ongoing lessons help them spot evolving scams that target current events or new platforms.
We know that no two teams are alike. That’s why our training is designed to cater to different learning styles—whether your employees prefer hands-on simulations, quick video tutorials, or detailed guides.
By addressing these differences, our program ensures that every member of your team is equipped to act as your first line of defense.
Cybercriminals are opportunists. They’ll exploit vulnerabilities in new devices, trends in the news, or even global events like pandemics to infiltrate businesses. Their tactics constantly evolve, but your defenses can too.
With Breach Secure Now, you’re not just reacting to threats—you’re staying ahead of them. From educating employees about phishing to implementing best practices for device security, we help you keep your business secure in an ever-changing landscape.
When you partner with Four Winds IT, you’re not just getting cutting-edge training programs—you’re gaining a team that integrates these tools into your overall cybersecurity strategy.
Whether you’re an established partner or exploring your options, we’ll guide you every step of the way.
Cybersecurity doesn’t have to be complicated—but it does require a proactive approach. By embracing awareness as a core element of your strategy, you empower your team to defend your business from the inside out.
Ready to get started?
When simplicity meets strategy, security becomes second nature. Partner with Four Winds IT and Breach Secure Now to make awareness your strongest defense.
Cybersecurity awareness training educates employees on recognizing and responding to cyber threats like phishing, ransomware, and data breaches. It's crucial because human error is the leading cause of security incidents. Awareness training helps prevent these mistakes by empowering your team with the knowledge to identify and mitigate risks.
Breach Secure Now’s training is continuous, interactive, and tailored to diverse learning styles. Unlike one-off training sessions, our program provides ongoing updates and simulations to keep your team prepared for the ever-evolving tactics of cybercriminals.
Many cyber insurance providers mandate awareness training as part of their risk management criteria. Training demonstrates that your organization is taking proactive steps to reduce the likelihood of a breach, which in turn reduces the insurer's risk exposure.
Cybersecurity training should be an ongoing process. While foundational training is essential, regular updates, simulations, and refresher courses ensure your team stays informed about new threats and best practices.
Our program incorporates multiple formats, including videos, quizzes, hands-on simulations, and guides. This ensures that every employee—whether they’re visual learners, hands-on practitioners, or quick readers—can engage with and retain the material effectively.
Employees should be able to recognize:
Awareness training is a critical component but should be part of a larger cybersecurity strategy. Combining training with tools like endpoint protection, firewalls, and monitoring ensures a comprehensive defense.
Many industries have strict compliance standards, such as HIPAA, GDPR, and PCI-DSS. Cybersecurity awareness training helps meet these requirements by addressing the human element of security, often a mandatory aspect of compliance audits.
Success can be measured through:
Four Winds IT offers a seamless integration of Breach Secure Now’s training into your overall cybersecurity strategy. We provide ongoing support, help track progress, and implement complementary security measures to enhance your business’s resilience against threats.

If your company uses Cleo software, it’s crucial to be aware of a recent vulnerability that could expose your business to cyber threats. A flaw in...

If there’s one thing every business loves, it’s a solid return on investment (ROI). But when it comes to cybersecurity, many see it as an expense...
In today’s fast-paced digital landscape, cyber threats evolve faster than yesterday’s memes. (Seriously!) The good news? SentinelOne’s AI-driven...